So, you're here to dive deep into the world of remote IoT SSH AWS example, huh? Well, buckle up because this is going to be one heck of a ride. In today's tech-driven world, connecting your IoT devices securely has become more important than ever. Whether you're managing smart home systems, industrial sensors, or any other IoT setup, mastering SSH on AWS can transform the way you handle remote operations. This guide will walk you through everything you need to know, from the basics to advanced techniques, so let's get started!
Now, why should you care about remote IoT SSH AWS example? Because, my friend, cybersecurity is no joke. If you're dealing with IoT devices, chances are they're spread across different locations, and securing them remotely is crucial. SSH (Secure Shell) is the go-to protocol for encrypted connections, and AWS provides a robust platform to manage all your IoT needs. Combine the two, and you've got a powerhouse setup that can protect your data while giving you full control over your devices.
But hold up, before we dive into the nitty-gritty, let's make sure we're on the same page. If you're new to this stuff, don't sweat it. This guide is designed to cater to both beginners and pros. We'll cover everything from setting up SSH keys to managing IoT devices on AWS, so even if you're just starting out, you'll leave here feeling like a tech wizard. Let's get rolling!
Read also:Patriots Eye Big Afc Trade The Move That Could Shake Up The Nfl
Here's a quick roadmap to what we'll cover:
- Understanding SSH and its role in IoT
- Why AWS is the perfect platform for IoT
- Step-by-step guide to setting up SSH on AWS
- Best practices for securing your IoT devices
- Real-world examples of remote IoT SSH AWS setups
What Is SSH and Why Does It Matter for IoT?
Alright, let's start with the basics. SSH, or Secure Shell, is a cryptographic network protocol that allows you to securely connect to remote devices. It's like having a secret tunnel between your computer and your IoT devices, where all the data flowing through is encrypted and protected from prying eyes. In the context of IoT, SSH is a game-changer because it ensures that your devices remain secure, even when accessed remotely.
Here's why SSH matters so much:
- Encryption: SSH encrypts all communication, making it nearly impossible for hackers to intercept your data.
- Authentication: SSH uses public and private keys to verify the identity of both the client and server, ensuring that only authorized users can access your devices.
- Command Execution: With SSH, you can execute commands on remote devices as if you were sitting right in front of them. This is super handy for managing IoT setups.
Now, if you're thinking, "Hey, why not just use plain old HTTP or FTP?" – well, here's the deal. Those protocols are not secure by default, which means anyone with the right tools can snoop on your data. SSH, on the other hand, is built with security in mind, making it the best choice for IoT applications.
SSH vs. Other Protocols: Why SSH Wins
Let's break it down real quick. Here's a comparison of SSH with some other popular protocols:
| Protocol | Security | Complexity | Use Case |
|---|---|---|---|
| SSH | High | Medium | Remote device management |
| HTTP | Low | Low | Web browsing |
| FTP | Very Low | Low | File transfers |
As you can see, SSH stands out when it comes to security, which is why it's the top choice for IoT applications.
Read also:Unveiling The Net Worth And Legacy Of Mike Tyson A Boxing Icon
Why AWS Is Perfect for IoT and SSH
Now that we've got SSH covered, let's talk about AWS. Amazon Web Services (AWS) is one of the leading cloud platforms in the world, and for good reason. It offers a wide range of services that make managing IoT devices a breeze. From IoT Core to Lambda functions, AWS has everything you need to build a scalable and secure IoT infrastructure.
Here's why AWS is the perfect platform for your remote IoT SSH AWS example:
- Scalability: AWS can handle thousands, if not millions, of IoT devices without breaking a sweat. Whether you're managing a small home setup or a large industrial network, AWS has got you covered.
- Security: AWS provides robust security features, including IAM roles, VPCs, and encryption, to ensure your data remains safe.
- Integration: AWS services like IoT Core and Lambda make it easy to integrate SSH with your IoT devices, streamlining the entire process.
But wait, there's more. AWS also offers monitoring tools like CloudWatch, which let you keep an eye on your devices in real-time. This means you can quickly detect and respond to any security threats, ensuring your IoT setup remains secure at all times.
AWS IoT Core: The Heart of Your IoT Setup
AWS IoT Core is one of the key services that make AWS so powerful for IoT applications. It acts as a bridge between your devices and the cloud, allowing you to securely connect, monitor, and manage your IoT devices. With IoT Core, you can:
- Connect millions of devices to the cloud
- Process and route device data
- Monitor device behavior in real-time
And the best part? It integrates seamlessly with SSH, making it super easy to manage your devices remotely.
Step-by-Step Guide to Setting Up SSH on AWS
Alright, let's get our hands dirty. Here's a step-by-step guide to setting up SSH on AWS for your IoT devices:
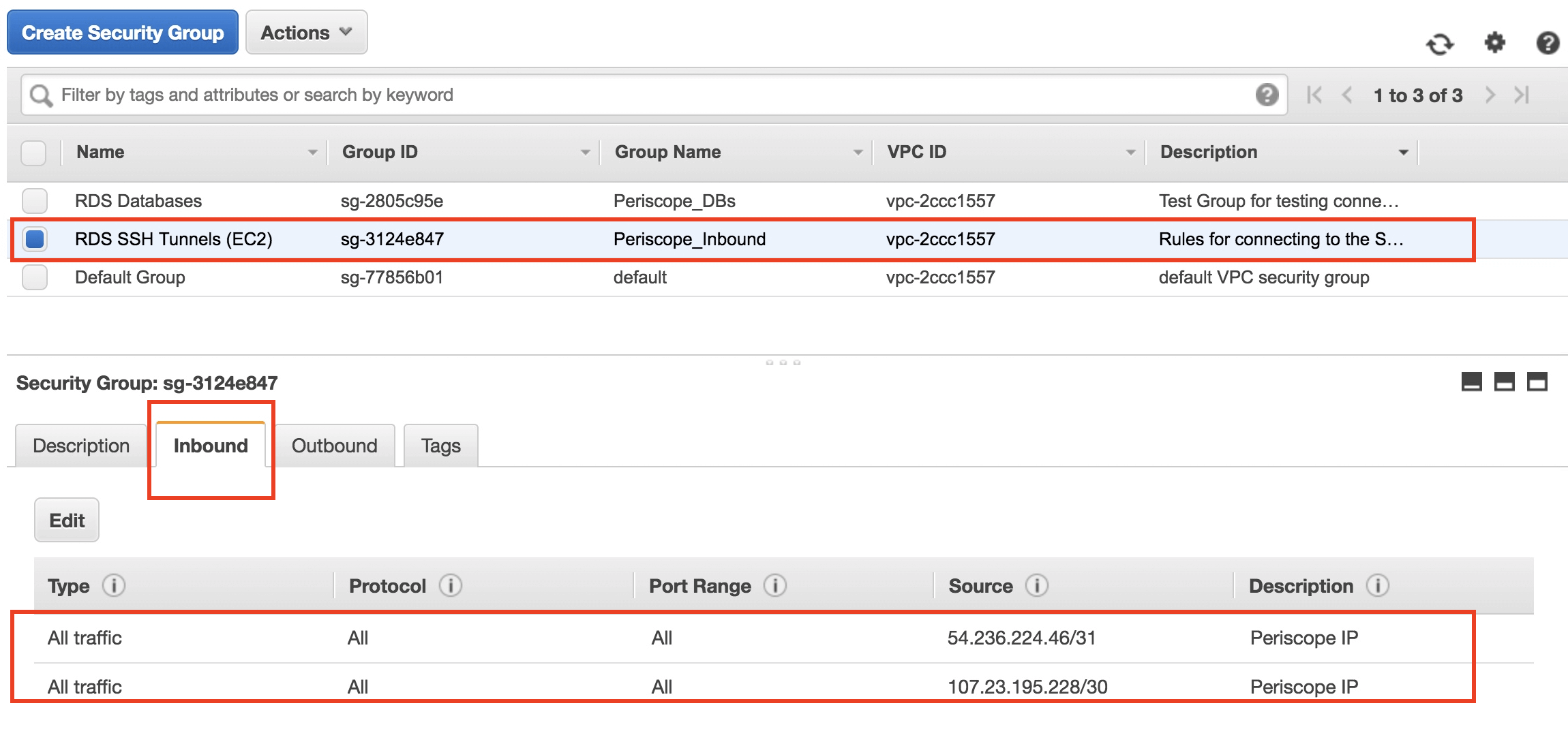
Step 1: Create an EC2 Instance
First things first, you'll need to create an EC2 instance on AWS. This will act as your server, where you'll connect to your IoT devices via SSH. Follow these steps:
- Log in to your AWS Management Console
- Go to the EC2 Dashboard
- Click on "Launch Instance" and choose an AMI (Amazon Machine Image)
- Configure the instance settings and security group
Make sure to allow SSH traffic in your security group settings. This will allow you to connect to your instance via SSH.
Step 2: Generate SSH Keys
Next, you'll need to generate SSH keys to securely connect to your EC2 instance. Here's how:
- Open your terminal or command prompt
- Type the following command:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com" - Follow the prompts to save the key pair
Once you've generated your keys, upload the public key to your EC2 instance. This will allow you to authenticate without needing a password.
Step 3: Connect to Your Instance via SSH
Now that everything's set up, it's time to connect to your instance. Here's how:
- Open your terminal or command prompt
- Type the following command:
ssh -i "your-key.pem" ec2-user@your-instance-public-ip - Enter your passphrase when prompted
And that's it! You're now connected to your EC2 instance via SSH.
Best Practices for Securing Your IoT Devices
Now that you've got SSH up and running, it's time to talk about security. Here are some best practices to keep your IoT devices safe:
- Use Strong Passwords: Always use strong, unique passwords for your devices and accounts.
- Enable Two-Factor Authentication: Add an extra layer of security by enabling 2FA wherever possible.
- Keep Software Updated: Regularly update your devices and software to patch any security vulnerabilities.
- Monitor Activity: Use tools like AWS CloudWatch to monitor your devices for any suspicious activity.
Remember, security is an ongoing process. Stay vigilant and keep an eye on your devices to ensure they remain safe.
Common Security Threats and How to Mitigate Them
Here are some common security threats you might face and how to deal with them:
- Brute Force Attacks: Use fail2ban or similar tools to block repeated login attempts.
- Man-in-the-Middle Attacks: Always use SSH to encrypt your connections.
- Malware: Regularly scan your devices for malware and remove any suspicious files.
By following these best practices, you can significantly reduce the risk of security breaches.
Real-World Examples of Remote IoT SSH AWS Setups
Let's take a look at some real-world examples of how people are using remote IoT SSH AWS example setups:
Example 1: Smart Home Automation
John, a tech enthusiast, uses AWS to manage his smart home devices. He sets up an EC2 instance and connects all his devices via SSH, allowing him to control them remotely from anywhere in the world. With AWS IoT Core, he can monitor his devices in real-time and automate tasks like turning off lights or adjusting the thermostat.
Example 2: Industrial Sensor Management
A manufacturing company uses AWS to manage thousands of sensors spread across their factories. By setting up SSH connections, they can securely access and manage each sensor, ensuring that all data is collected and analyzed accurately. This setup helps them optimize their operations and reduce downtime.
These examples show just how versatile and powerful the combination of SSH and AWS can be for IoT applications.
Conclusion: Take Action Today!
And there you have it – your ultimate guide to remote IoT SSH AWS example. From understanding SSH and AWS to setting up your own secure connections, we've covered everything you need to know to get started. Remember, security is key when it comes to IoT, so always follow best practices and stay vigilant.
Now, it's your turn to take action. Whether you're setting up a smart home or managing industrial sensors, the tools and knowledge are at your fingertips. So, what are you waiting for? Get out there and start building your secure IoT setup today!
Before you go, don't forget to leave a comment below and let us know what you think. Also, feel free to share this article with your friends and colleagues. The more people know about secure IoT setups, the better!